An Empirical Analysis of Traceability in the Monero Blockchain
Authors: Malte Möser (Princeton University), Kyle Soska (Carnegie Mellon University), Ethan Heilman (Boston University), Kevin Lee (University of Illinois at Urbana-Champaign), Henry Heffan (Brookline High School), Shashvat Srivastava (Massachusetts Academy of Math and Science at WPI), Kyle Hogan (Massachusetts Institute of Technology), Jason Hennessey (Boston University), Andrew Miller (University of Illinois at Urbana-Champaign), Arvind Narayanan (Princeton University), Nicolas Christin (Carnegie Mellon University)
Volume: 2018
Issue: 3
Pages: 143–163
DOI: https://doi.org/10.1515/popets-2018-0025
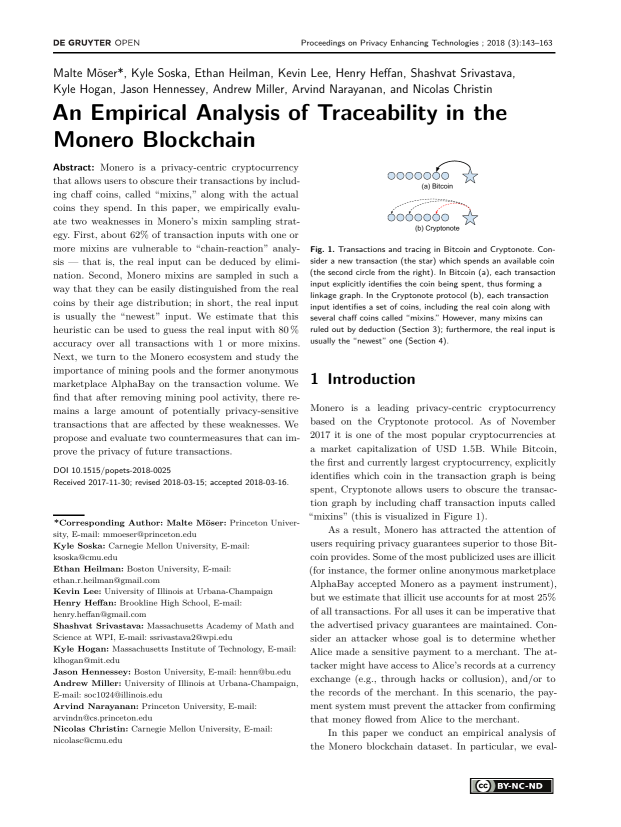
Abstract: Monero is a privacy-centric cryptocurrency that allows users to obscure their transactions by including chaff coins, called “mixins,” along with the actual coins they spend. In this paper, we empirically evaluate two weaknesses in Monero’s mixin sampling strategy. First, about 62% of transaction inputs with one or more mixins are vulnerable to “chain-reaction” analysis — that is, the real input can be deduced by elimination. Second, Monero mixins are sampled in such a way that they can be easily distinguished from the real coins by their age distribution; in short, the real input is usually the “newest” input. We estimate that this heuristic can be used to guess the real input with 80 % accuracy over all transactions with 1 or more mixins. Next, we turn to the Monero ecosystem and study the importance of mining pools and the former anonymous marketplace AlphaBay on the transaction volume. We find that after removing mining pool activity, there remains a large amount of potentially privacy-sensitive transactions that are affected by these weaknesses. We propose and evaluate two countermeasures that can improve the privacy of future transactions.
Copyright in PoPETs articles are held by their authors. This article is published under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 license.